NIST Cybersecurity Framework 2.0 Reveals Major Shifts in Federal Guidance
On February 26, 2024, the National Institute of Standards and Technology (NIST) released the Cybersecurity Framework version 2.0 (CSF 2.0). CSF 2.0 is a generational update to NIST’s foundational cybersecurity guidance, which was last updated in April 2018 (version 1.1) (CSF 1.1). Risk governance and supply chain risk management comprise the most significant changes from CSF 1.1 to 2.0. In this blog post, we look at what the CSF 2.0 means for organizations, and what executives and cybersecurity professionals should be thinking about as they integrate this new guidance into existing cybersecurity risk management programs. We note that NIST is also seeking public comments on a guide for developing Community Profiles by May 3, 2024.
What is the CSF?
CSF 2.0 is the culmination of years of collaborative work between NIST, the private sector, and other government agencies around the world. Like its predecessor, CSF 2.0 is intended to provide risk-based, flexible guidance for organizations to manage cybersecurity risks. It outlines a set of cybersecurity activities, outcomes, and informative references that are common across organizations. Although not intended by NIST to be a maturity model, many organizations use the CSF to measure their security programs and gauge their progress in implementing cybersecurity risk management practices.
The CSF 2.0 has multiple components: a “Framework Core,” “Implementation Tiers,” and “Framework Profiles,” along with guidance on mapping the CSF 2.0 to other resources, and a discussion of how to use the CSF to communicate internally and externally to an organization, its suppliers, and partners about risk management. The Framework Core (see graphic below) describes a set of cybersecurity outcomes, organized by Function, Category, and Subcategory.
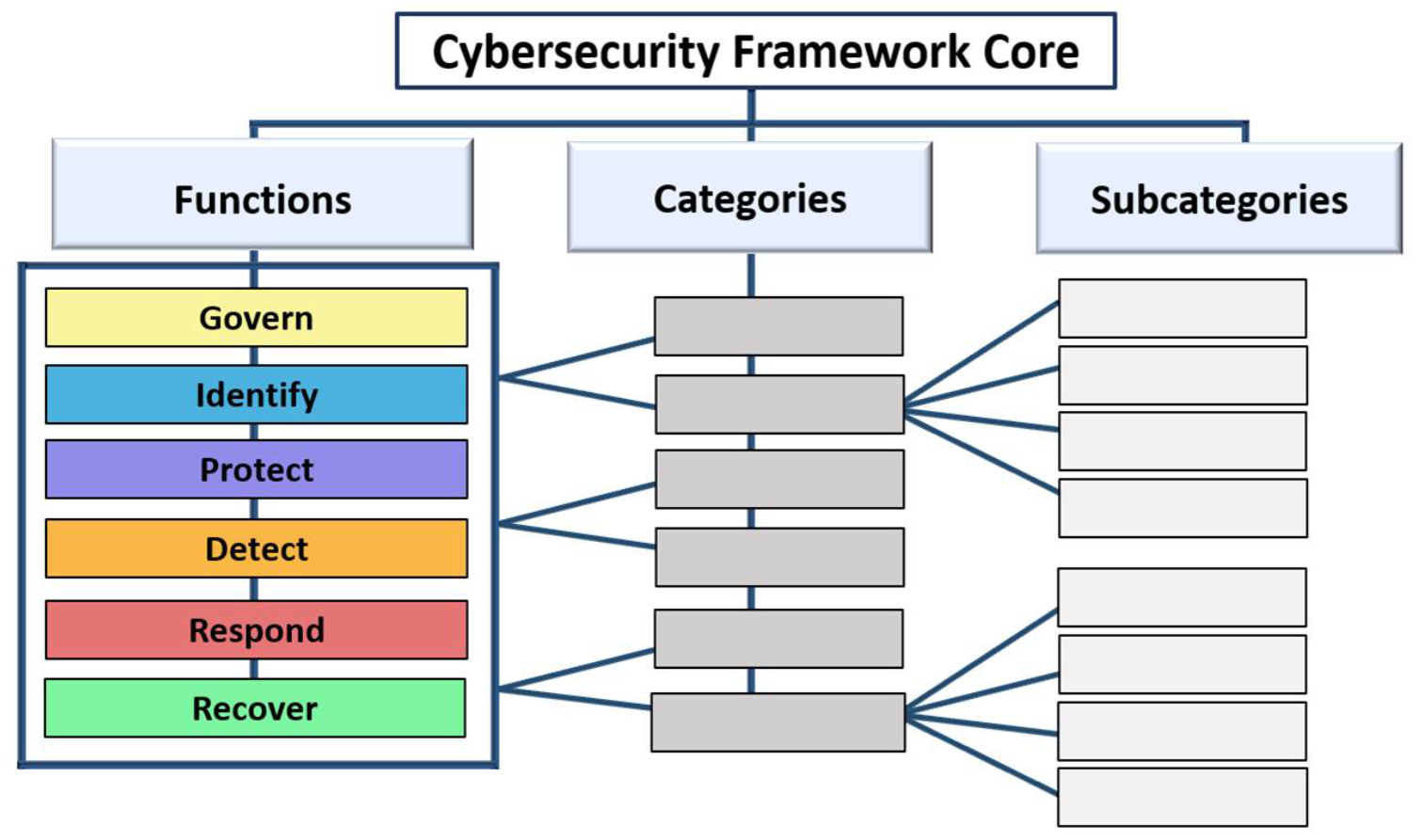
What has changed between CSF 1.1 and CSF 2.0?
The biggest structural change made from CSF 1.1 to CSF 2.0 is the addition of a new Function: Govern. CSF 2.0 also reorganizes, adds, and/or edits several Categories and Subcategories. The new Govern Function contains the most significant additions and reorganizations in a new Category focused on cybersecurity supply chain risk management (C-SCRM). This new material reflects evolving expectations about third-party and supply chain risk management, adding outcomes for due diligence, assessment of business partners for criticality, and lifecycle management. CSF 2.0 also adds new outcomes on protecting against unauthorized software and integrating secure software development practices.
NIST has also developed new and updated explanatory materials to accompany the CSF 2.0, including Profile templates, “quick start guides” for creating different types of Profiles, and explanatory material around Tiers and using CSF 2.0 for C-SCRM and Enterprise Risk Management. NIST is also seeking public comments on a guide for developing Community Profiles (i.e., mapping the CSF 2.0 to an industry sector, organization type, or other profile intended to be used by various organizations such as sector agencies, industries, or trade associations to address sector specific risks). NIST has also built new functionality into the online resource Informative References and has added Implementation Examples that are intended to provide illustrations and explanations of how an organization might implement the Subcategories.
What Should Organizations Be Doing Now with CSF 2.0?
Many organizations use the CSF as a baseline for their cybersecurity risk management programs. Now is the time to update risk management frameworks and internal programs to match the new content and organization of CSF 2.0. Organizations should examine the CSF 2.0 and incorporate new and amended material to the extent it is relevant to that organization. The CSF 2.0 reflects evolving expectations around governance, supply chain risk management, and secure software development—these should be focus areas for updating the scope and content of existing risk management programs. Organizations should also consider how the CSF 2.0 guidance interacts with new federal requirements, such as cyber governance disclosures and incident reporting for Securities and Exchange Commission filers, cyber incident reporting for critical infrastructure (pending a rulemaking from the Department of Homeland Security’s Cybersecurity and Infrastructure Agency), and evolving federal guidance on supply chain risk management and secure software development.
Will the CSF 2.0 Be the Baseline for Future Cybersecurity Regulations?
There is increasing interest from the U.S. government in establishing mandatory cybersecurity baselines for regulated companies. The National Cybersecurity Strategy Implementation Plan tasks NIST with helping agencies align regulations with the CSF and other international standards. The Federal Communications Commission (FCC), for example, has begun to require recipients of certain FCC program funding to submit and certify cybersecurity risk management plans that are based on the CSF.
Regardless of industry sector, companies should review the CSF 2.0, incorporate the changes into their cybersecurity risk management activities, and consider how they might need to adapt or expand those activities if required by a regulator to demonstrate adoption of the CSF 2.0. Building an individual or Community Profile using NIST’s guidance is one way to examine how CSF 2.0 outcomes would be applied and prioritized for a particular company, industry, or sector. There is a fundamental tension between NIST’s flexible, intentionally non-regulatory approach to the CSF and establishing it as a regulatory baseline. Companies should be prepared to advocate to sector regulators how to retain the benefits of the CSF’s flexible and risk-based approach that allows outcomes to be tailored for a company’s unique threat picture, operations, and capabilities.





